Reset Credentials
Reset Credentials job is actually a multi-purpose, all-in-one function. It can be used to update a credential or generate a new on.
Also it is possible to set a new credential too. We are able to reset (or update) the credential in the local database or to change them on the remote targets as well.
Navigate to the Accounts main tab and select the context menu by clicking on the icon under the Actions column. Select Reset Credentials.
You can also navigate to the Accounts pop-up window (Targets main tab / Context menu / Accounts) and click on the icon under the Actions column and select: Reset credentials.
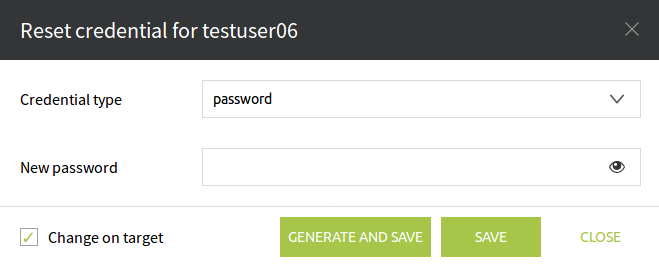
A window will pop-up with the Reset credential for (account_name) title.
If there are several types of SSH keys associated with the account, you can choose from them in the list. The available SSH types are:
- ssh-rsa (this is the 'default' SSH key as named previously)
- ecdsa-sha2-nistp256
- ssh-dss
- ssh-ed25519
Under the Credential type we can select the credential we want to update (password, SSH-key, PIN number, etc). In the input field named New password we can enter the new credential which will overwrite the existing one. To make sure that it has not been miss-typed click on the icon to show on the screen what you have just entered in that field.
Generate and Save button (as its name says) it generates a credential using the policy settings and will save it as well. Next time we run a CheckOut Credential job this newly generated credential will be displayed.
If we only want to change the credential in the database, the check-box Change on target has to be unchecked. This function can be used if we have got an Account which is not InSync, but we know the right credential to get it InSync again.