3. SecPol (SAM) Settings
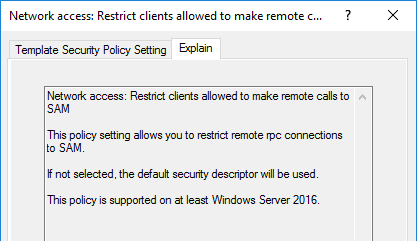
Restrict clients allowed to make remote calls to SAM
For the RCP-client, some additional settings are required on Microsoft Windows targets (for more information, please click on the link: Restrict clients allowed to make remote calls to SAM ):
Type 'secpol.msc' in the start menu search field, and open the App:
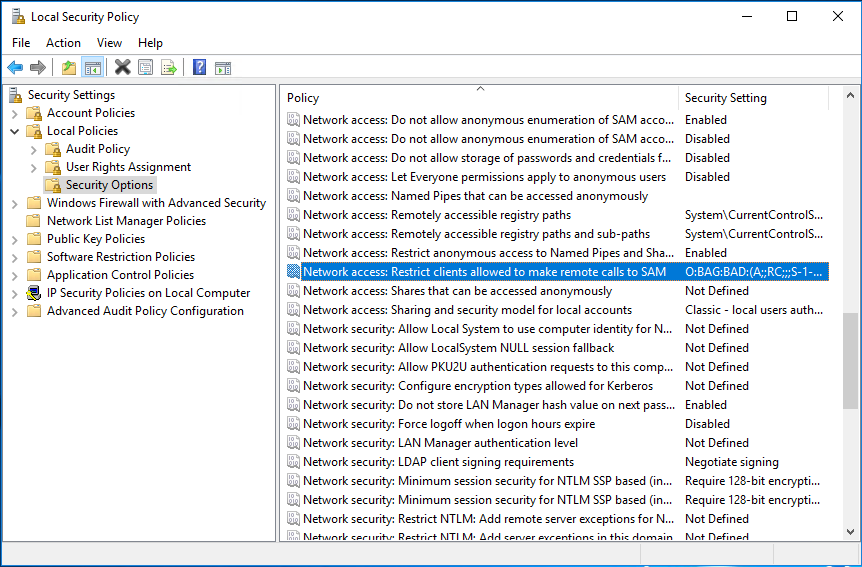
Visit this section: Security Settings / Local Policies / Security Options
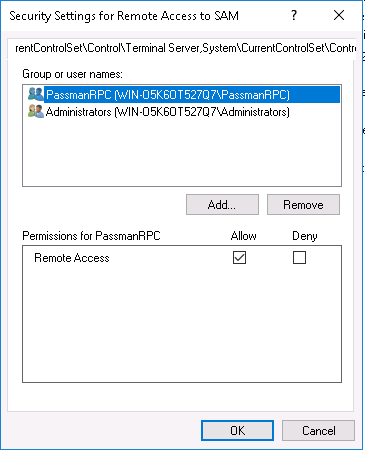
Find this Policy at the right tab (pressing 'n' makes it easier): 'Network access: Restrict clients allowed to make remote calls to SAM'
At the beginning, its Security Setting status will be: Not defined
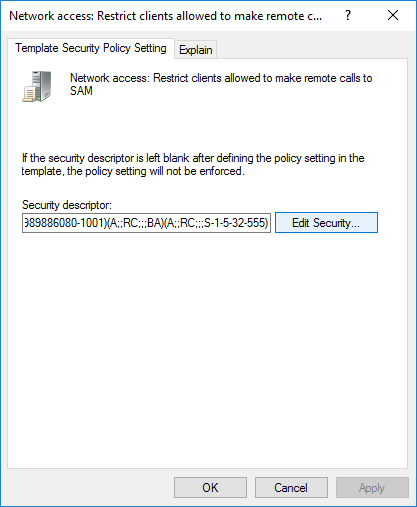
Double-click on that entry, and Edit Security...
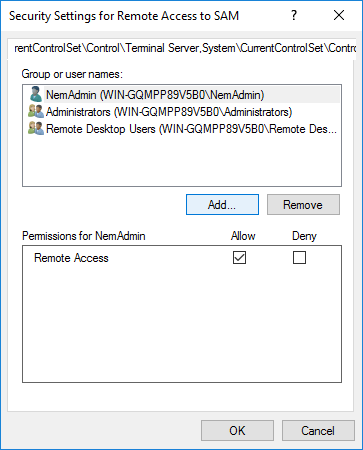
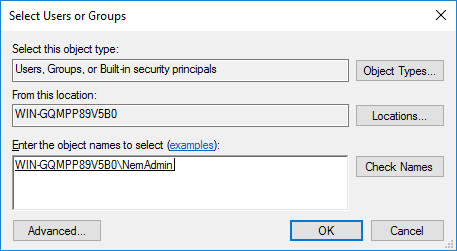
Use the Add... button to recognise groups or individual accounts to be added. (this way the RCP-client will receive access to change their passwords)
5. We recommend adding account names separately to ensure they will receive the rights.
Once the setup is finished, the Security Setting status will display hexadecimal keys.
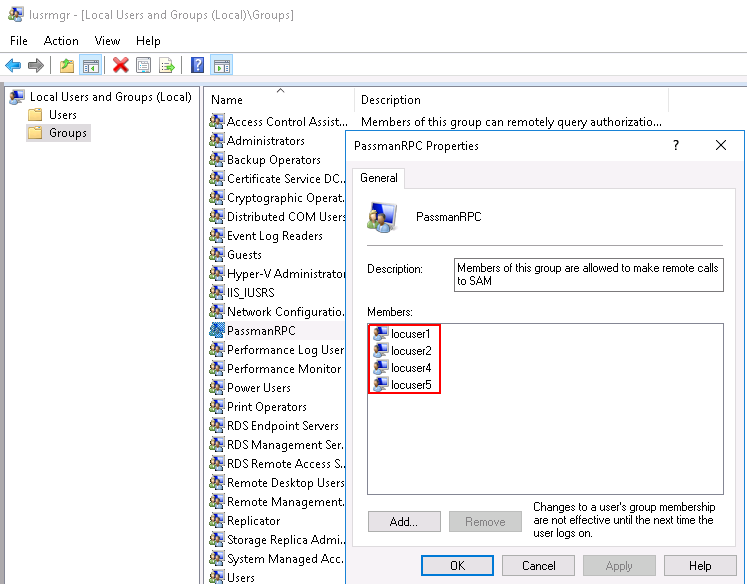
SAM settings by defining new groups (optional)
For ease of user management, it is advised to create a separate group, then add this group to the list. To create a group, navigate to Local Users and Groups window - or simply run the lusrmgr.mcs command in the command line. Next, add the users (that we want to manage in PassMan) to this group.
Finally the group has to be added to the security settings, as it is shown on the screenshot below.
For Microsoft Windows 10 (version 1607) and Microsoft Windows Server 2016, these adjustments must be completed.
On these versions the default settings had been changed, so only the built-in Administrator group has got all these privileges. (On the Domain Controller (DC) machines, these settings had not been changed, meaning all users can (by default) use Remote Access.) Important to note, older versions of Microsoft Windows also include these settings and an Administrator can overwrite the default Security Descriptor settings anytime. This indicates that in a real-life situation it might occur as a highly common problem.